Are You Managing the Hidden Costs of Public Docker Images?

⚠️ Note: signal.fyi shut down date: October 2025.
Attribution to Source Research
This blog draws heavily from Chainguard’s True Cost of Vulnerability Management Report, a detailed study on the hidden time and resource costs associated with container vulnerability management. By using Chainguard’s data as a foundation, we’ve calculated the estimated annual costs of managing public Docker images and demonstrated how automation tools like signal.fyi can alleviate these burdens.
1. Introduction: Why Public Docker Images Aren’t Really Free
"Public Docker images seem free upfront, but what’s the hidden cost in terms of operational inefficiency, security risk, and compliance effort?"
For smaller teams, the challenge of managing public Docker images can feel insurmountable compared to the resources available to larger companies. These larger organizations often dedicate entire teams to compliance, security, and vulnerability management. But what happens when your team doesn’t have those resources?
With signal.fyi, these costs are reduced through automated public reporting, actionable PRs, and SBOM generation—enabling teams to maintain compliance and transparency effortlessly:
- Tracking vulnerabilities across images.
- Preparing documentation for audits.
- Maintaining a consistent and transparent security posture.
signal.fyi addresses these specific challenges for public Docker images. While it doesn’t fix vulnerabilities, it ensures teams can:
- Gain visibility into their current risks.
- Track progress toward a stronger security posture.
- Maintain audit-ready compliance without excessive manual work.
2. How Vulnerability Management Creates Hidden Costs
"We’ve been managing public Docker image compliance manually—what’s the real impact on our team’s efficiency and scalability?"
Managing vulnerabilities in public Docker images requires ongoing time and effort. While larger organizations often dedicate entire teams to this work, smaller teams with fewer resources face significant challenges.
In teams without automation, managing public Docker images can be labor-intensive, including:
- Significant hours spent identifying and triaging vulnerabilities manually.
- Extensive time preparing compliance documentation, such as SBOMs, for audits.
- Continuous effort to maintain transparency and build trust with stakeholders.
Cost Breakdown Table
To ensure transparency, this cost breakdown table is rooted in findings from Appendix 1 of Chainguard’s True Cost of Vulnerability Management Report.
These estimates are calculated based on real-world examples of time spent annually on vulnerability management by organizations of varying sizes. For access, readers can sign up for free with their email, providing valuable context and deeper insights.
| Cost Element | Details | Estimated Annual Cost Per Image | Appendix Reference |
|---|---|---|---|
| Vulnerability Tracking (CVE Management) | Based on smaller organizations in the report (e.g., Observability Company, Developer Tools Company). | $3,000–$5,000 | Observability Company, Developer Tools Company |
| - 2–3 hours/week on CVE triage. 2.5 hours/week × 50 weeks × $75/hour = ~$9,375/year. | Developer Tools Company | ||
| - For smaller teams, time is spread across fewer images, leading to ~$3,000–$5,000/image. | Observability Company | ||
| Compliance Preparation | Derived from examples like Application Development Platform and IT Consulting Company. | $1,750–$3,500 | Application Development Platform, IT Consulting Company |
| - Preparing SBOMs, reports, and audits: ~200–1,000 hours/year across teams. | Application Development Platform | ||
| - Averaged at 35 hours/image/year × $75/hour = ~$2,625/year per image. | IT Consulting Company | ||
| Missed Opportunities to Improve | Gaps in visibility or poor tracking (e.g., U.S. Federal Organization). | Intangible but critical | U.S. Federal Organization |
| - Lost efficiency: Time spent repeatedly assessing similar risks. | U.S. Federal Organization | ||
| - No measurable ROI on security improvements due to inconsistent tracking. | U.S. Federal Organization | ||
| Debugging Upstream Issues | Lightly referenced in the data; minimal for most cases. | Not explicitly calculated here | Not Applicable |
| Total Annual Cost Per Image | Combined vulnerability tracking and compliance costs. | $4,750–$8,500+ | Aggregated from above |
Transparency in Cost Breakdown
The following cost estimates are derived directly from Appendix 1 of Chainguard’s True Cost of Vulnerability Management Report. These examples provide real-world context for understanding the annual effort and associated costs of managing vulnerabilities:
From Appendix 1:
- Transport & Logistics Company: ~20,000 hours annually
- U.S. Federal Organization: ~15,000 hours annually
- IT Consulting Company: ~1,000 hours annually
These numbers form the foundation of our analysis, adapted to focus specifically on the costs of managing public Docker images.
1. Vulnerability Tracking (CVE Management)
Examples Used:
- Observability Company: 2 hours/week × 50 weeks = ~100 hours/year.
- Developer Tools Company: 2–3 hours/week × 50 weeks = ~150 hours/year.
These examples reflect smaller organizations with limited resources dedicated to CVE triage. Their workload aligns with the scale of teams managing fewer public Docker images, resulting in $3,000–$5,000 annually per image, assuming $75/hour for engineering time.
2. Compliance Preparation
Examples Used:
- Application Development Platform: 16 hours/month × 12 months = ~200 hours/year.
- IT Consulting Company: ~20 hours/week × 50 weeks = ~1,000 hours/year.
These organizations illustrate the time-intensive nature of preparing SBOMs, audit reports, and other compliance artifacts. The chosen average of 35 hours/year per image provides a balanced estimate for smaller teams, resulting in ~$2,625 per image annually.
3. Missed Opportunities to Improve
Example Used:
- U.S. Federal Organization: 15 security engineers dedicating 20 hours/week = ~15,000 hours/year.
This example highlights inefficiencies caused by repeated triage efforts without effective tracking mechanisms. The inefficiencies illustrated are relevant to organizations of all sizes, often leading to critical, intangible costs.
4. Debugging Upstream Issues
Reason for Limited Inclusion:
While upstream issues were lightly mentioned in Appendix 1, specific calculations were not provided. Their impact, though minimal compared to other costs, is acknowledged as a potential disruption for teams relying on external image updates.
"The real cost of managing public Docker images isn’t just time or money—it’s the missed opportunity to organize, improve, and demonstrate progress toward better security practices."
3. Why SBOMs Matter in Vulnerability Management
"SBOMs provide critical visibility into what we’re running. Even if we aim for zero CVEs, don’t we still need this level of transparency?"
A Software Bill of Materials (SBOM) is a detailed inventory of what’s inside your public Docker images. SBOMs play a critical role in managing vulnerabilities by:
- Identifying risks within each layer of your public Docker images.
- Communicating security posture to stakeholders and regulators.
- Supporting audit readiness by documenting the contents of your images.
But if your team achieves zero CVEs with hardened images, does the SBOM still matter?
Yes—SBOMs remain valuable for:
- Ensuring Transparency: Proving to stakeholders that your images remain secure.
- Tracking New Changes: As base images evolve, SBOMs help identify new risks quickly.
- Building Trust: Demonstrating a commitment to proactive security measures.
signal.fyi simplifies SBOM generation, ensuring you always have an up-to-date, compliance-ready report.
4. Why Not Just Switch to Zero-CVE Containers?
"Switching to zero-CVE containers is a great goal—but what’s the plan to get there, and how do we manage compliance during the transition?"
Zero-CVE containers are an ideal goal, but for most teams, reaching that goal is a journey requiring:
- Evaluating Current Risks: Without visibility into your existing vulnerabilities, it’s hard to prioritize effectively.
- Incremental Migration: Moving towards more secure images requires testing and validating changes to avoid disruption.
- Maintaining Communication: During the transition, teams need to keep stakeholders informed about progress.
Steps to Chart Your Progress Toward Zero CVEs
- Track Your Current State
- signal.fyi identifies vulnerabilities in your public Docker images and provides a clear baseline to work from.
- Map Out Improvements
- Rather than focusing exclusively on high-risk vulnerabilities, signal.fyi monitors changes to parent images, enabling your team to transition to more secure options while maintaining a comprehensive record of the process.
- Enable Transparent Reporting
- signal.fyi's Public Reports and Dashboard offer transparency, letting you share SBOM updates and insights with stakeholders—no logins needed. Team members also gain PR insights, with vulnerability summaries and digest tracking integrated directly into workflows.
- Recognize and Celebrate Progress
- With historical tracking and reporting, signal.fyi helps your team showcase security posture improvements, boosting morale and trust.
5. The Value Beyond Zero CVEs
"If we achieve zero CVEs, does signal.fyi still provide value by supporting compliance and simplifying reporting?"
Yes—signal.fyi continues to deliver value by:
- Providing Continuous Compliance
- Automated reports ensure audit readiness, even after reaching zero CVEs.
- Maintaining Visibility
- Changes upstream are tracked and documented directly in source code via pull requests against your default branch.
- Enabling Accountability
- Building Trust and Morale
- Tracking progress allows teams to highlight their hard work, fostering recognition and engagement internally and externally.
6. signal.fyi: Public Dashboards, Reports, and Pull Requests in Action
"What does this look like in practice?"
With signal.fyi, teams gain access to:
- Public Dashboards: Transparent, no-login-required views of compliance updates and SBOM changes, empowering teams and stakeholders with instant access to critical information. See dashboard.
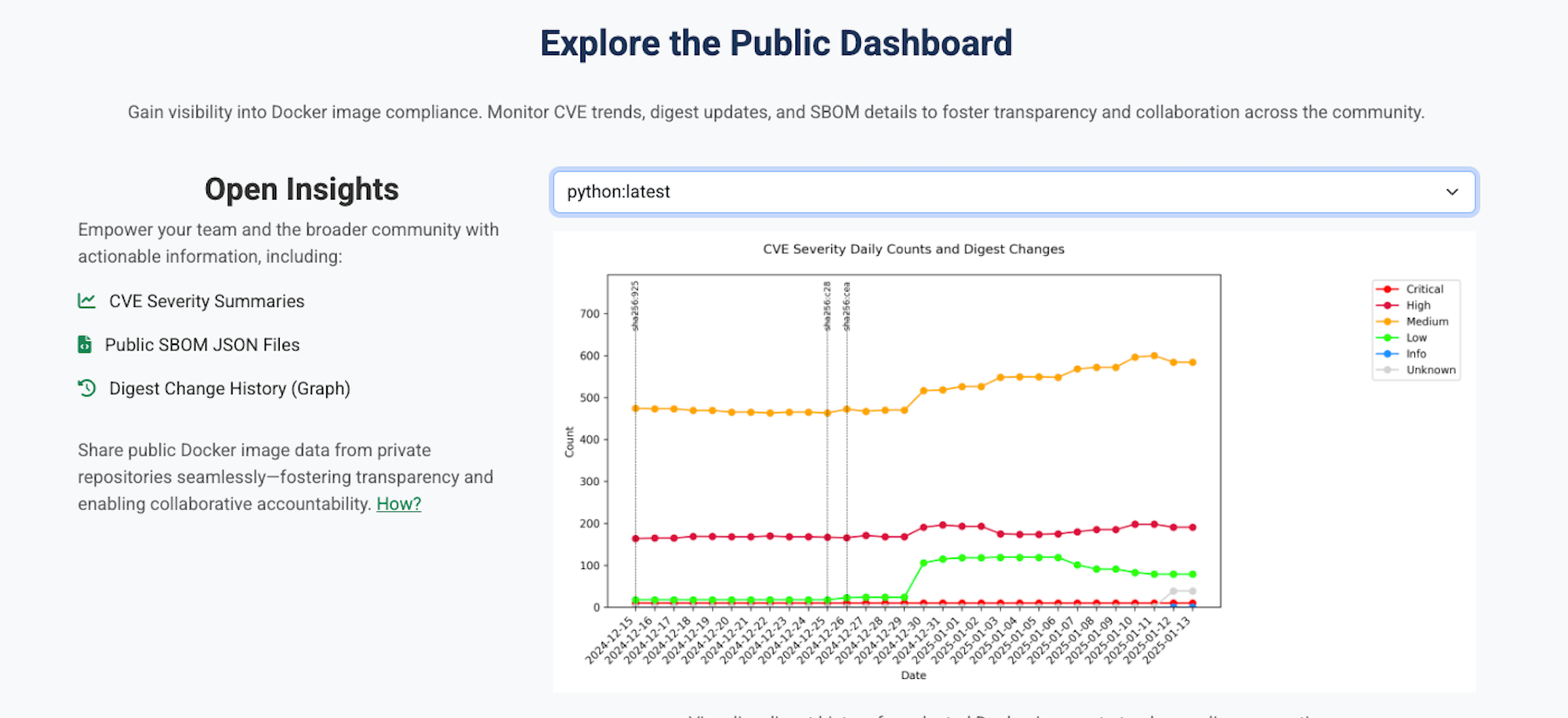
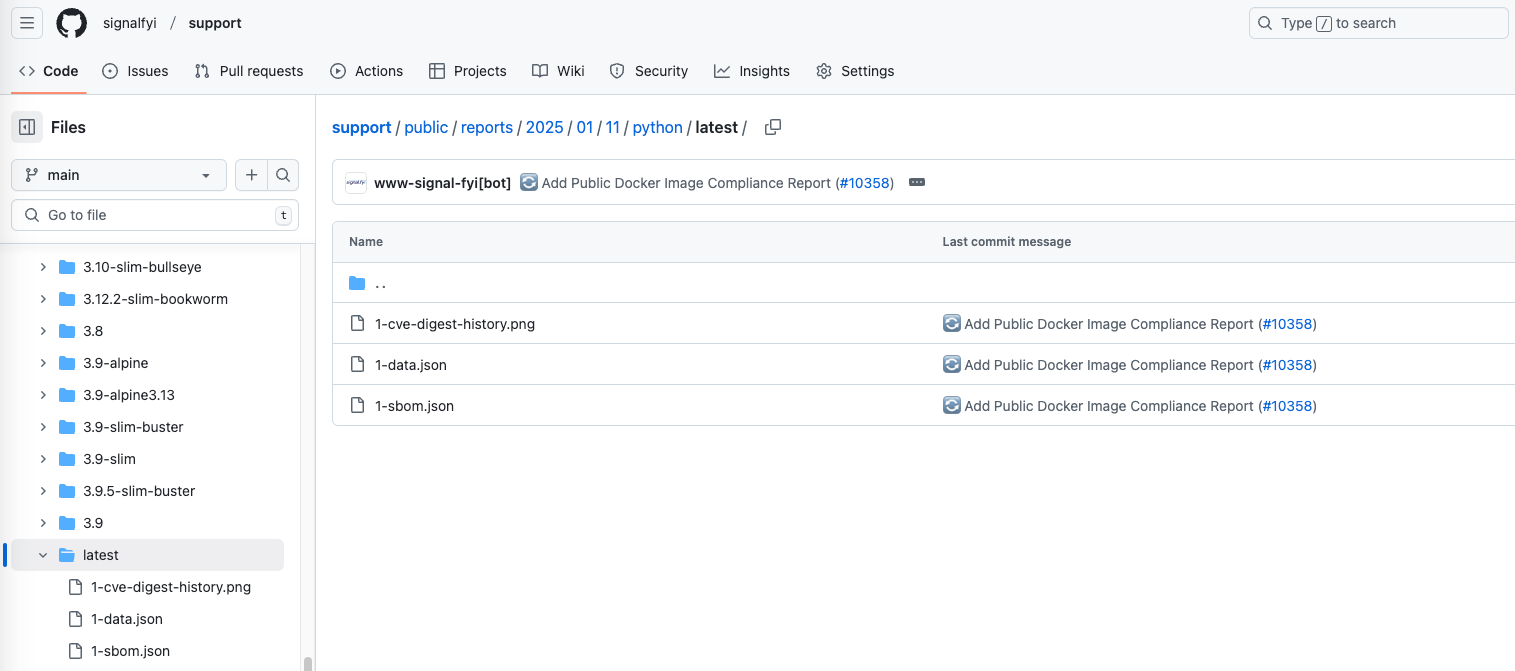
- On-Demand Reporting: Shareable reports that showcase your team’s progress and improvements. See our public reports.
- Pull Request Enrichment: Clear summaries of vulnerabilities and image changes embedded directly in your development workflow. Set up before you can brew a cup of coffee. Receive your first pull request before tomorrow's stand-up.
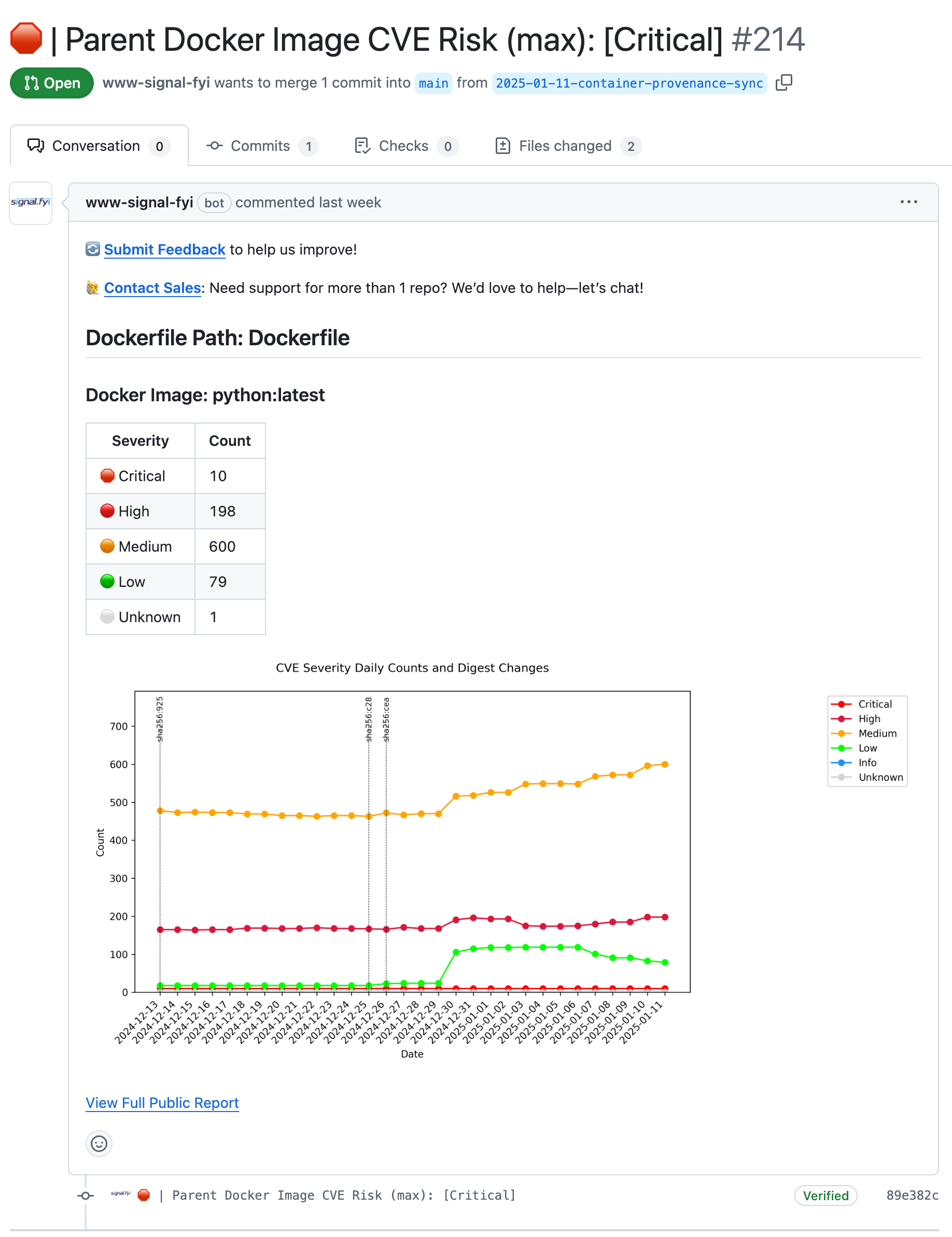
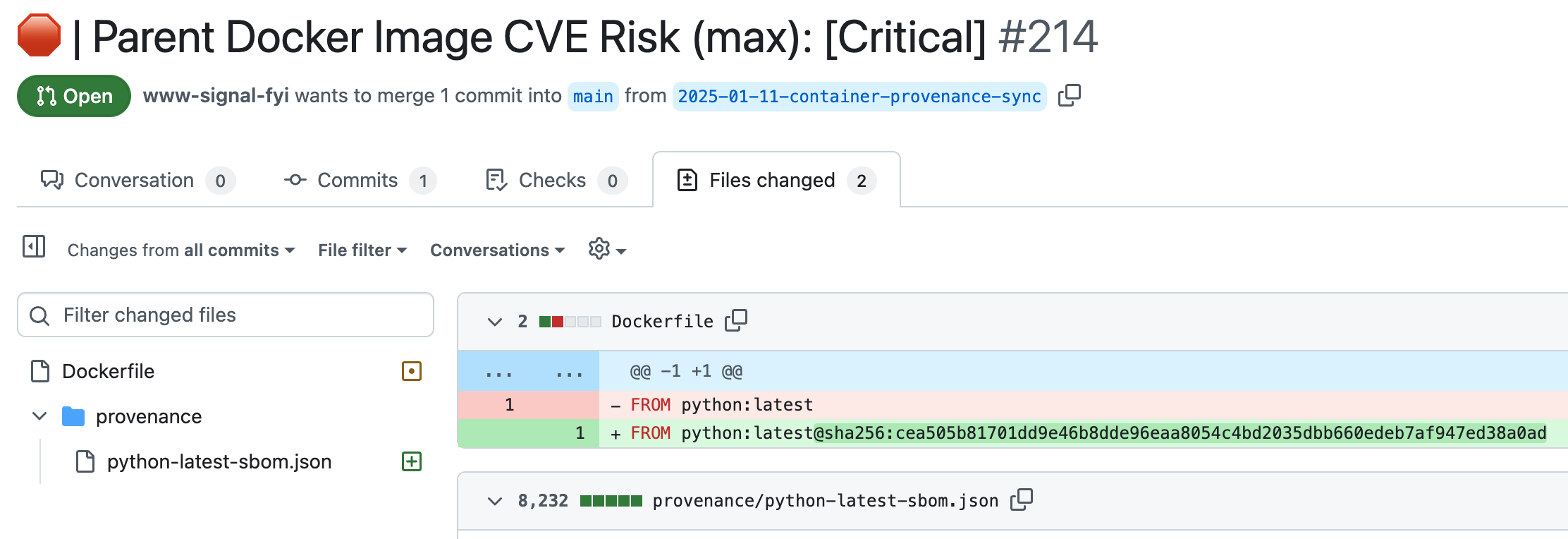
Pull requests enriched by signal.fyi summarize vulnerabilities and parent image changes, giving engineers the context they need to make informed decisions quickly.
"I’ll be honest—tracking the version of our parent Docker image in our source code wasn’t even on my radar. But the more I think about it, every version change shifts our security posture and potentially impacts our app’s functionality. signal.fyi’s enriched pull requests surface this critical data, giving us a clear way to measure and track these changes—something we weren’t doing before. By building an audit trail of these version updates, we’re not just responding to risks; we’re proactively aligning with the Secure Software Development Framework (SSDF) by improving visibility, auditability, and decision-making at every step."
7. Closing: Managing Public Docker Images Effectively
"We’ve been using public Docker images for years—but are we managing them in a way that supports compliance and improves security?"
signal.fyi helps teams:
- Gain continuous visibility into vulnerabilities and changes in public Docker images, with actionable insights delivered directly to your workflows to strengthen your security posture.
- Simplify compliance workflows with public dashboards and reports that require no login credentials—ensuring transparency without unnecessary barriers.
- Track and share progress with stakeholders, demonstrating a commitment to security and building trust both internally and externally.
Whether you’re addressing today’s vulnerabilities or planning for future compliance needs, signal.fyi provides the automation, transparency, and insights your team needs to stay ahead.



